Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 41:
The Chief Information Security Officer for an organization recently received approval to install a new EDR solution. Following the installation, the number of alerts that require remediation by an analyst has tripled. Which of the following should the organization utilize to best centralize the workload for the internal security team? (Select two).
A. SOAR
B. SIEM
C. MSP
D. NGFW
E. XDR
F. DLP
-
Question 42:
Using open-source intelligence gathered from technical forums, a threat actor compiles and tests a malicious downloader to ensure it will not be detected by the victim organization's endpoint security protections. Which of the following stages of the Cyber Kill Chain best aligns with the threat actor's actions?
A. Delivery
B. Reconnaissance
C. Exploitation
D. Weaponizatign
-
Question 43:
An incident responder was able to recover a binary file through the network traffic. The binary file was also found in some machines with anomalous behavior. Which of the following processes most likely can be performed to understand the purpose of the binary file?
A. File debugging
B. Traffic analysis
C. Reverse engineering
D. Machine isolation
-
Question 44:
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
A. Registry changes or anomalies
B. Data exfiltration
C. Unauthorized privileges
D. File configuration changes
-
Question 45:
An organization has established a formal change management process after experiencing several critical system failures over the past year. Which of the following are key factors that the change management process will include in order to reduce the impact of system failures? (Select two).
A. Ensure users the document system recovery plan prior to deployment.
B. Perform a full system-level backup following the change.
C. Leverage an audit tool to identify changes that are being made.
D. Identify assets with dependence that could be impacted by the change.
E. Require diagrams to be completed for all critical systems.
F. Ensure that all assets are properly listed in the inventory management system.
-
Question 46:
A security analyst scans a host and generates the following output:
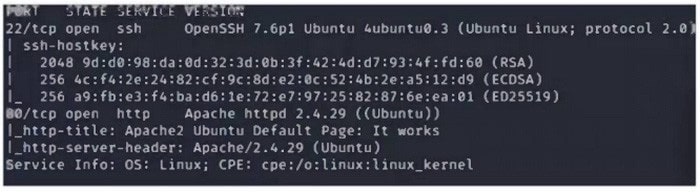
Which of the following best describes the output?
A. The host is unresponsive to the ICMP request.
B. The host Is running a vulnerable mall server.
C. The host Is allowlng unsecured FTP connectlons.
D. The host is vulnerable to web-based exploits.
-
Question 47:
A security analyst has received an incident case regarding malware spreading out of control on a customer's network. The analyst is unsure how to respond. The configured EDR has automatically obtained a sample of the malware and its signature. Which of the following should the analyst perform next to determine the type of malware, based on its telemetry?
A. Cross-reference the signature with open-source threat intelligence.
B. Configure the EDR to perform a full scan.
C. Transfer the malware to a sandbox environment.
D. Log in to the affected systems and run necstat.
-
Question 48:
During an incident, analysts need to rapidly investigate by the investigation and leadership teams. Which of the following best describes how PII should be safeguarded during an incident?
A. Implement data encryption and close the data so only the company has access.
B. Ensure permissions are limited in the investigation team and encrypt the data.
C. Implement data encryption and create a standardized procedure for deleting data that is no longer needed.
D. Ensure that permissions are open only to the company.
-
Question 49:
An analyst views the following log entries:
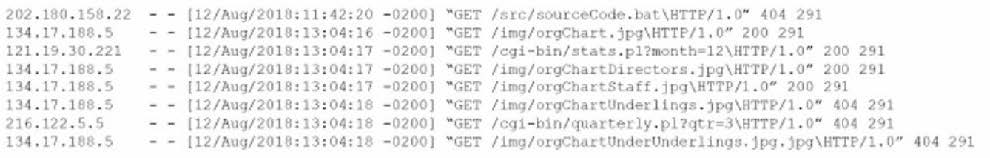
The organization has a partner vendor with hosts in the 216.122.5.x range. This partner vendor is required to have access to monthly reports and is the only external vendor with authorized access. The organization prioritizes incident investigation according to the following hierarchy:
1.
unauthorized data disclosure is more critical than denial of service attempts
2.
which are more important than ensuring vendor data access
Based on the log files and the organization's priorities, which of the following hosts warrants additional investigation?
A. 121.19.30.221
B. 134.17.188.5
C. 202.180.1582
D. 216.122.5.5
-
Question 50:
A SOC analyst is analyzing traffic on a network and notices an unauthorized scan. Which of the following types of activities is being observed?
A. Potential precursor to an attack
B. Unauthorized peer-to-peer communication
C. Rogue device on the network
D. System updates
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.