Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 291:
While reviewing system logs, a network administrator discovers the following entry:
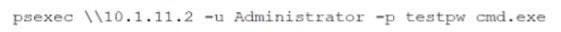
Which of the following occurred?
A. An attempt was made to access a remote workstation.
B. The PsExec services failed to execute.
C. A remote shell failed to open.
D. A user was trying to download a password file from a remote system.
-
Question 292:
A security analyst is analyzing the following output from the Spider tab of OWASP ZAP after a vulnerability scan was completed:
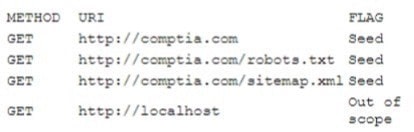
Which of the following options can the analyst conclude based on the provided output?
A. The scanning vendor used robots to make the scanning job faster
B. The scanning job was successfully completed, and no vulnerabilities were detected
C. The scanning job did not successfully complete due to an out of scope error
D. The scanner executed a crawl process to discover pages to be assessed
-
Question 293:
An organization implemented an extensive firewall access-control blocklist to prevent internal network ranges from communicating with a list of IP addresses of known command-and-control domains A security analyst wants to reduce the load on the firewall. Which of the following can the analyst implement to achieve similar protection and reduce the load on the firewall?
A. A DLP system
B. DNS sinkholing
C. IP address allow list
D. An inline IDS
-
Question 294:
Which of the following describes the difference between intentional and unintentional insider threats'?
A. Their access levels will be different
B. The risk factor will be the same
C. Their behavior will be different
D. The rate of occurrence will be the same
-
Question 295:
Which of the following is the BEST option to protect a web application against CSRF attacks?
A. Update the web application to the latest version.
B. Set a server-side rate limit for CSRF token generation.
C. Avoid the transmission of CSRF tokens using cookies.
D. Configure the web application to only use HTTPS and TLS 1.3.
-
Question 296:
The management team has asked a senior security engineer to explore DLP security solutions for the company's growing use of cloud-based storage. Which of the following is an appropriate solution to control the sensitive data that is being stored in the cloud?
A. NAC
B. IPS
C. CASB
D. WAF
-
Question 297:
An organization announces that all employees will need to work remotely for an extended period of time. All employees will be provided with a laptop and supported hardware to facilitate this requirement. The organization asks the information security division to reduce the risk during this time. Which of the following is a technical control that will reduce the risk of data loss if a laptop is lost or stolen?
A. Requiring the use of the corporate VPN
B. Requiring the screen to be locked after five minutes of inactivity
C. Requiring the laptop to be locked in a cabinet when not in use
D. Requiring full disk encryption
-
Question 298:
A security analyst is logged on to a jump server to audit the system configuration and status. The organization's policies for access to and configuration of the jump server include the following:
1.
No network access is allowed to the internet.
2.
SSH is only for management of the server.
3.
Users must utilize their own accounts, with no direct login as an administrator.
4.
Unnecessary services must be disabled.
The analyst runs netstar with elevated permissions and receives the following output:
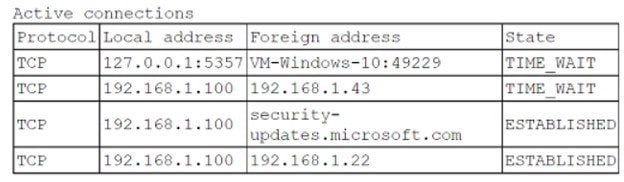
Which of the following policies does the server violate?
A. Unnecessary services must be disabled.
B. SSH is only for management of the server.
C. No network access is allowed to the internet.
D. Users must utilize their own accounts, with no direct login as an administrator.
-
Question 299:
While observing several host machines, a security analyst notices a program is overwriting data to a buffer. Which of the following controls will best mitigate this issue?
A. Data execution prevention
B. Output encoding
C. Prepared statements
D. Parameterized queries
-
Question 300:
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts The company's AUP and code of conduct prohibits this practice.
Which of the following configuration changes would improve security and help prevent this from occurring?
A. Configure the DLP transport rules to provide deep content analysis.
B. Put employees' personal email accounts on the mail server on a blocklist.
C. Set up IPS to scan for outbound emails containing names and contact information.
D. Use Group Policy to prevent users from copying and pasting information into emails.
E. Move outbound emails containing names and contact information to a sandbox for further examination.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.