Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Jun 28, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 301:
Given the output below:
#nmap 7.70 scan initiated Tues, Feb 8 12:34:56 2022 as: nmap -v -Pn -p 80,8000,443 --script http-* -oA server.out 192.168.220.42
Which of the following is being performed?
A. Cross-site scripting
B. Local file inclusion attack
C. Log4] check
D. Web server enumeration
-
Question 302:
During the forensic analysis of a compromised machine, a security analyst discovers some binaries that are exhibiting abnormal behaviors. After extracting the strings, the analyst finds unexpected content. Which of the following is the next step the analyst should take?
A. Validate the binaries' hashes from a trusted source.
B. Use file integrity monitoring to validate the digital signature
C. Run an antivirus against the binaries to check for malware.
D. Only allow binaries on the approve list to execute.
-
Question 303:
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
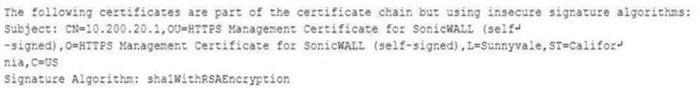
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A. Reconfigure the device to support only connections leveraging TLSv1.2.
B. Obtain a new self-signed certificate and select AES as the hashing algorithm.
C. Replace the existing certificate with a certificate that uses only MD5 for signing.
D. Use only signed certificates with cryptographically secure certificate sources.
-
Question 304:
A security engineer is reviewing security products that identify malicious actions by users as part of a company's insider threat program. Which of the following is the most appropriate product category for this purpose?
A. SCAP
B. SOAR
C. UEBA
D. WAF
-
Question 305:
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH D. Modbus
-
Question 306:
A security analyst wants to capture large amounts of network data that will be analyzed at a later time. The packet capture does not need to be in a format that is readable by humans, since it will be put into a binary file called "packetCapture." The capture must be as efficient as possible, and the analyst wants to minimize the likelihood that packets will be missed. Which of the following commands will best accomplish the analyst's objectives?
A. tcpdump -w packetCapture
B. tcpdump -a packetCapture
C. tcpdump -n packetCapture
D. nmap -v > packetCapture
E. nmap -oA > packetCapture
-
Question 307:
A security analyst responds to a series of events surrounding sporadic bandwidth consumption from an endpoint device. The security analyst then identifies the following additional details:
1.
Bursts of network utilization occur approximately every seven days.
2.
The content being transferred appears to be encrypted or obfuscated.
3.
A separate but persistent outbound TCP connection from the host to infrastructure in a third-party cloud is in place.
4.
The HDD utilization on the device grows by 10GB to 12GB over the course of every seven days.
5.
Single file sizes are 10GB.
Which of the following describes the most likely cause of the issue?
A. Memory consumption
B. Non-standard port usage
C. Data exfiltration
D. System update
E. Botnet participant
-
Question 308:
A security analyst is reviewing the following log entries to identify anomalous activity:
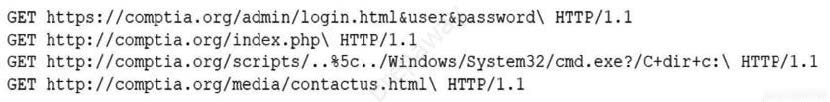
Which of the following attack types is occurring?
A. Directory traversal
B. SQL injection
C. Buffer overflow
D. Cross-site scripting
-
Question 309:
Given the Nmap request below:
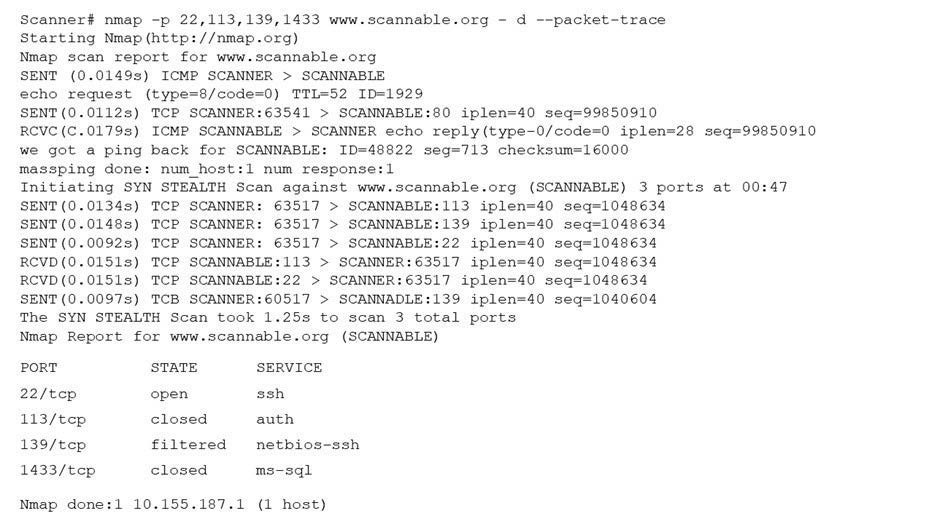
Which of the following actions will an attacker be able to initiate directly against this host?
A. Password sniffing
B. ARP spoofing
C. A brute-force attack
D. An SQL injection
-
Question 310:
A company's legal department is concerned that its incident response plan does not cover the countless ways security incidents can occur. The department has asked a security analyst to help tailor the response plan to provide broad coverage for many situations. Which of the following is the best way to achieve this goal?
A. Focus on incidents that have a high chance of reputation harm.
B. Focus on common attack vectors first.
C. Focus on incidents that affect critical systems.
D. Focus on incidents that may require law enforcement support.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.