Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:556 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 311:
During a company's most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
1.
The development team used a new software language that was not supported by the security team's automated assessment tools.
2.
During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected.
3.
The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
-
Question 312:
Legacy medical equipment, which contains sensitive data, cannot be patched. Which of the following is the best solution to improve the equipment's security posture?
A. Move the legacy systems behind a WAR
B. Implement an air gap for the legacy systems.
C. Place the legacy systems in the perimeter network.
D. Implement a VPN between the legacy systems and the local network.
-
Question 313:
A security analyst notices the following proxy log entries:
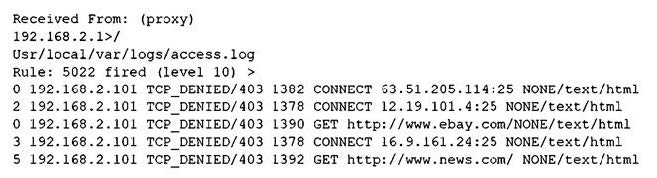
Which of the following is the user attempting to do based on the log entries?
A. Use a DoS attack on external hosts.
B. Exfiltrate data.
C. Scan the network.
D. Relay email.
-
Question 314:
Which of the following is a reason to take a DevSecOps approach to a software assurance program?
A. To find and fix security vulnerabilities earlier in the development process
B. To speed up user acceptance testing in order to deliver the code to production faster
C. To separate continuous integration from continuous development in the SDLC
D. To increase the number of security-related bug fixes worked on by developers
-
Question 315:
A consumer credit card database was compromised, and multiple representatives are unable to review the appropriate customer information. Which of the following should the cybersecurity analyst do first?
A. Start the containment effort.
B. Confirm the incident.
C. Notify local law enforcement officials.
D. Inform the senior management team.
-
Question 316:
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network. Which of the following technologies should the analyst recommend?
A. UEBA
B. DLP
C. NAC
D. EDR
-
Question 317:
Security awareness and compliance programs are most effective at reducing the likelihood and impact of attacks from:
A. advanced persistent threats.
B. corporate spies.
C. hacktivists.
D. insider threats.
-
Question 318:
A security analyst needs to recommend a solution that will allow users at a company to access cloud-based SaaS services but also prevent them from uploading and exfiltrating data. Which of the following solutions should the security analyst recommend?
A. CASB
B. MFA
C. VPN
D. VPS
E. DLP
-
Question 319:
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IoC list for monitoring. Which of the following is the best suggestion for improving monitoring capabilities?
A. Update the IPS and IDS with the latest rule sets from the provider.
B. Create an automated script to update the IPS and IDS rule sets.
C. Use an automated subscription to select threat feeds for IDS.
D. Implement an automated malware solution on the IPS.
-
Question 320:
A Chief Information Security Officer is concerned that contract developers may be able to steal the code used to design the company's latest application since they are able to pull code from a cloud-based repository directly to laptops that are not owned by the company. Which of the following solutions would best protect the company code from being stolen?
A. MDM
B. SCA
C. CASB
D. VDI
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.