Exam Details
Exam Code
:CS0-003Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:509 Q&AsLast Updated
:Mar 31, 2025
CompTIA CompTIA Certifications CS0-003 Questions & Answers
-
Question 361:
Which of the following BEST explains the function of a managerial control?
A. To scope the security planning, program development, and maintenance of the security life cycle
B. To guide the development of training, education, security awareness programs, and system maintenance
C. To implement data classification, risk assessments, security control reviews, and contingency planning
D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
-
Question 362:
Which of the following provides an automated approach to checking a system configuration?
A. SCAP
B. CI/CD
C. OVAL
D. Scripting
E. SOAR
-
Question 363:
A security analyst discovers the company's website is vulnerable to cross-site scripting. Which of the following solutions will BEST remedy the vulnerability?
A. Prepared statements
B. Server-side input validation
C. Client-side input encoding
D. Disabled JavaScript filtering
-
Question 364:
During a company's most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
The development team used a new software language that was not supported by the security team's automated assessment tools.
During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected. The current IPS did not have effective
signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment-tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
-
Question 365:
A security team is struggling with alert fatigue, and the Chief Information Security Officer has decided to purchase a SOAR platform to alleviate this issue. Which of the following BEST describes how a SOAR platform will help the security team?
A. SOAR will integrate threat intelligence into the alerts, which will help the security team decide which events should be investigated first.
B. A SOAR platform connects the SOC with the asset database, enabling the security team to make informed decisions immediately based on asset criticality.
C. The security team will be able to use the SOAR framework to integrate the SIEM with a TAXII server, which has an automated intelligence feed that will enhance the alert data.
D. Logic can now be created that will allow the SOAR platform to block specific traffic at the firewall according to predefined event triggers and actions.
-
Question 366:
An analyst needs to forensically examine a Windows machine that was compromised by a threat actor. Intelligence reports state this specific threat actor is characterized by hiding malicious artifacts, especially with alternate data streams. Based on this intelligence, which of the following BEST explains alternate data streams?
A. A different way data can be streamlined if the user wants to use less memory on a Windows system for forking resources.
B. A way to store data on an external drive attached to a Windows machine that is not readily accessible to users.
C. A Windows attribute that provides for forking resources and is potentially used to hide the presence of secret or malicious files inside the file records of a benign file.
D. A Windows attribute that can be used by attackers to hide malicious files within system memory.
-
Question 367:
A security analyst discovers a standard user has unauthorized access to the command prompt, PowerShell, and other system utilities. Which of the following is the BEST action for the security analyst to take?
A. Disable the appropriate settings in the administrative template of the Group Policy.
B. Use AppLocker to create a set of whitelist and blacklist rules specific to group membership.
C. Modify the registry keys that correlate with the access settings for the System32 directory.
D. Remove the user's permissions from the various system executables.
-
Question 368:
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
A. Keeping IPS rules up to date
B. Installing a proxy server
C. Applying network segmentation
D. Updating the antivirus software
-
Question 369:
A security analyst is supporting an embedded software team. Which of the following is the best recommendation to ensure proper error handling at runtime?
A. Perform static code analysis.
B. Require application fuzzing.
C. Enforce input validation.
D. Perform a code review.
-
Question 370:
The steering committee for information security management annually reviews the security incident register for the organization to look for trends and systematic issues. The steering committee wants to rank the risks based on past incidents to improve the security program for next year. Below is the incident register for the organization:
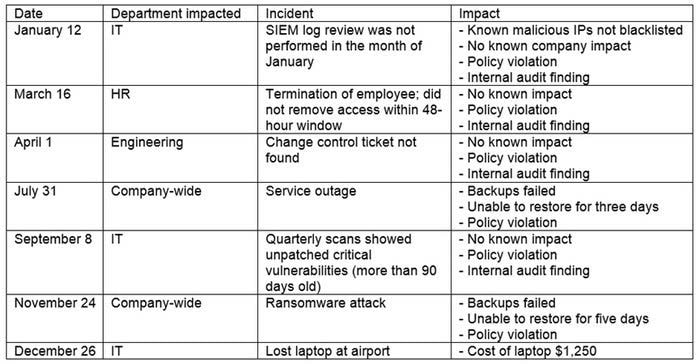
Which of the following should the organization consider investing in first due to the potential impact of availability?
A. Hire a managed service provider to help with vulnerability management.
B. Build a warm site in case of system outages.
C. Invest in a failover and redundant system, as necessary.
D. Hire additional staff for the IT department to assist with vulnerability management and log review.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.