Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 30, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 361:
According to CVSS, what is the attack vector?
A. set of steps taken by a threat actor before exploiting the vulnerability
B. process by which an attacker tries to exploit an existing vulnerability
C. context by which vulnerability exploitation is achievable
D. practical demonstration of an attack to understand the required tools and resources
-
Question 362:
What is the difference between SIEM and SOAR?
A. SOAR generates and prevents security alerts, and SIEM predicts attack patterns and applies the mitigation.
B. SOAR is more efficient in event gathering and analysis, and SIEM has an advantage in resource usage and anomaly detection speed.
C. The primary function of SIEM is to collect and detect events, and SOAR is more focused on workflows, threat detection, and remediation.
D. SIEM analyzes infrastructure and network traffic behavior for anomaly detection, and SOAR detects anomalies in known signatures.
-
Question 363:
What are the three critical security principles or goals of the CIA triad?
A. Protect the confidentiality of data, and ensure that protected data is unaltered at all stages and available for permitted requesters.
B. Validate the copyright of the data, and ensure that individual data owners are protected with a defense-in-depth approach.
C. Ensure that the connections are safe and the data delivery is improved continuously with appropriate monitoring and cross-checks.
D. Implement data tags to identify critical assets and data for preserving the secretness, and develop policies and procedures for accessing data.
-
Question 364:
A CMS plugin creates two files that are accessible from the Internet: myplugin.html and exploitable.php. A newly discovered exploit takes advantage of an injection vulnerability in exploitable.php. To exploit the vulnerability, an HTTP POST must be sent with specific variables to exploitable.php. A security engineer notices traffic to the webserver that consists of only HTTP GET requests to myplugin.html. Which category does this activity fall under?
A. exploitation
B. reconnaissance
C. installation
D. weaponization
-
Question 365:
Which statement describes threat hunting?
A. It is an activity by an entity to deliberately bring down critical internal servers.
B. It includes any activity that might go after competitors and adversaries to infiltrate their systems.
C. It is a vulnerability assessment conducted by cyber professionals.
D. It is a prevention activity to detect signs of intrusion, compromise, data theft, abnormalities, or malicious activity.
-
Question 366:
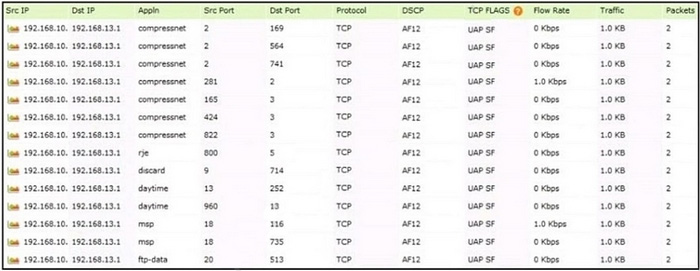
Refer to the exhibit. Which tool was used to generate this data?
A. NetFlow
B. dnstools
C. firewall
D. tcpdump
-
Question 367:
Which evasion method involves performing actions slower than normal to prevent detection?
A. timing attack
B. traffic fragmentation
C. resource exhaustion
D. tunneling
-
Question 368:
After a large influx of network traffic to externally facing devices, a security engineer begins investigating what appears to be a denial of service attack. When the packet capture data is reviewed, the engineer notices that the traffic is a single SYN packet to each port. Which type of attack is occurring?
A. traffic fragmentation
B. port scanning
C. host profiling
D. SYN flood
-
Question 369:
What is the dataflow set in the NetFlow flow-record format?
A. Dataflow set is a collection of HEX records.
B. Dataflow set provides basic information about the packet, such as the NetFlow version.
C. Dataflow set is a collection of binary patterns.
D. Dataflow set is a collection of data records.
-
Question 370:

Refer to the exhibit. Which attack is being attempted against a web application?
A. command injection
B. man-in-the-middle
C. denial of service
D. SQL injection
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.