Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:Mar 30, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 381:
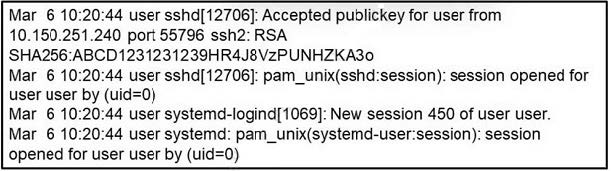
Refer to the exhibit. What occurred on this system based on this output?
A. A user connected to the system using remote access VPN.
B. A user connected to the system after 450 attempts.
C. A user connected to the system using SSH using source port 55796.
D. A user created a new HTTP session using the SHA256 hashing algorithm.
-
Question 382:
Which type of evasion technique is accomplished by separating the traffic into smaller segments before transmitting across the network?
A. encryption
B. tunneling
C. proxies
D. fragmentation
-
Question 383:
What is a Shellshock vulnerability?
A. command injection
B. cross site scripting
C. heap overflow
D. SQL injection
-
Question 384:
What is the impact of encapsulation on the network?
A. Numerous local private addresses are mapped to a public one before the data is moved.
B. Something significant is concealed from virtually separate networks.
C. Web requests are taken on behalf of users and the response is collected from the web.
D. Logically separate functions in the network are abstracted from their underlying structures.
-
Question 385:
An analyst performs traffic analysis to detect data exfiltration and identifies a high frequency of DNS requests in a small period of time. Which technology makes this behavior feasible?
A. access control list
B. NAT
C. encryption
D. tunneling
-
Question 386:
What describes the usage of a rootkit in endpoint-based attacks?
A. remote code execution that causes a denial-of-service on the system
B. exploit that can be used to perform remote code execution
C. set of vulnerabilities used by an attacker to disable root access on the system
D. set of tools used by an attacker to maintain control of a compromised system while avoiding detection
-
Question 387:
Which type of attack involves executing arbitrary commands on the operating system to escalate privileges?
A. Apache log
B. cross-site scripting
C. command injection
D. SQL injection
-
Question 388:
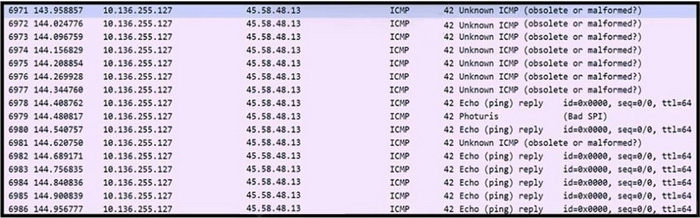
Refer to the exhibit. An engineer received a ticket to analyze unusual network traffic. What is occurring?
A. data exfiltration
B. regular network traffic; no suspicious activity
C. denial-of-service attack
D. cookie poisoning
-
Question 389:
Which type of data is used to monitor and detect anomalies within the organization's network?
A. statistical
B. metadata
C. transaction
D. alert
-
Question 390:
Which statement describes indicators of attack?
A. A malicious file is detected by the AV software.
B. Internal hosts communicate with countries outside of the business range.
C. Phishing attempts on an organization are blocked by mail AV.
D. Critical patches are missing.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.